GET request to the target server. While this process appears simple, uncovering a vulnerability in this flow generally result in an account takeover, giving unauthorized access to user accounts.The program stated that disclosing the report is not permitted, so for now we'll consider the target as . If you happen to discover the real target mentioned anywhere on this blog, please let me know. I can't promise anything, but a reward might be waiting for you.
Recently, I discovered a vulnerability while connecting Google accounts on .com leading to a one-click account takeover on .
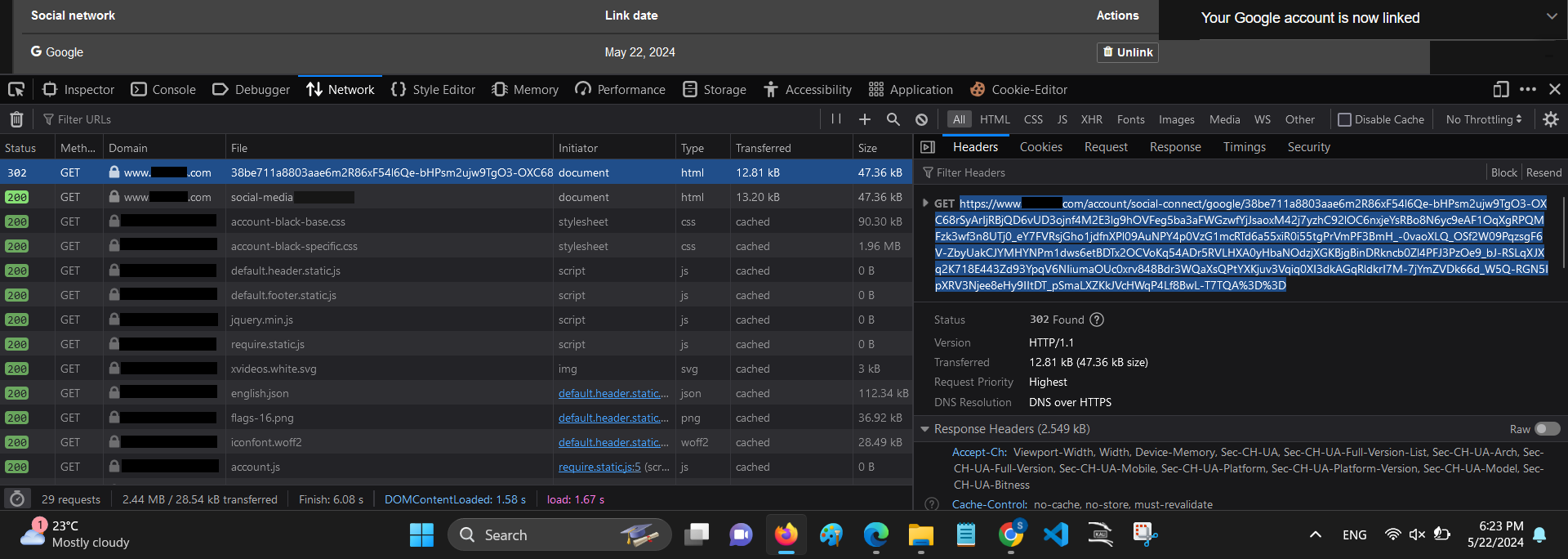
The working mechanism of "Social Network Sign in" in case of :
While connecting a Google account on my account, first a
At last, a final
 |
While connecting a Google account on my account, first a
GET request was sent to Google with a consent to connect the Google account, and a 302 redirect with auth code was returned i.e. https://www. .com/account/social-connect/google?state=664cd32c3ee7f&code=482FOAdL IrYfimwLsCndVmIYjHkIRX1VWc02b9rPtBheLxFiQa9XJpmSGWt92JiV_juKmUl5uog&scope=email+profile+https83A82F82Fwww.googleapis.com82Fauth82Fuserinfo.profile+https83A82F82Fwww.googleapis.com%2Fauth%2Fuserinfo.email+openid&authuser=2&prompt=none |
And upon sending a
GET request to .com with that auth code, there was another 302 redirect https:// .com/account/social-connect/google/0b96f5c3ef391a5cQxHZRTXgbdN9ibq3NbFBxzsBYuwt3TeyFT87rV CdAQDyF6m32u9ABHs1WHOHfzYWKd5AWBOvcM5PzcdCoifAsVWrvyVES7vj6zgmPdlPEcf7o0VjFHWViUtUqGx zSALbziATACzBgJZcGanJf65NRhNiOqMfuZ1Y00iw_WV7WNOdxzwAw4bz I9q8hL3 JaJI7BwZ 67MDs8 yHXmIn4 ox014T9QAxkj4NRaVOZBDcXn-SDd1E4aSxcE5etFsmt1035VYw41MVFLK_KHidUDuXXd-x5EYc045V_XznxQsSUMuPfzkqvycQ3MkB6fOoiL6_mxqDt0eMlmWEJv7ILAfKm6ZllyBGBfLZ-XvZOnrm549x8yvw0hH2M12b22RhFZC81BZXSul-E2lleb5eOnGCBI3jBwALKWReJOpuZ85w9rvpqp3evN4MrDffjp70vbcG7K9ebXx6GHxAT5v0iftCkaMQ&3D%3D |
At last, a final
GET request on https:// .com/account/social-connect/google/0b96f5c3ef391a5cQxHZRTXgbdN9ibq3NbFBxzsBYuwt3TeyFT87rV CdAQDyF6m32u9ABHs1WHOHfzYWKd5AWBOvcM5PzcdCoifAsVWrvyVES7vj6zgmPdlPEcf7o0VjFHWViUtUqGx zSALbziATACzBgJZcGanJf65NRhNiOqMfuZ1Y00iw_WV7WNOdxzwAw4bz I9q8hL3 JaJI7BwZ 67MDs8 yHXmIn4 ox014T9QAxkj4NRaVOZBDcXn-SDd1E4aSxcE5etFsmt1035VYw41MVFLK_KHidUDuXXd-x5EYc045V_XznxQsSUMuPfzkqvycQ3MkB6fOoiL6_mxqDt0eMlmWEJv7ILAfKm6ZllyBGBfLZ-XvZOnrm549x8yvw0hH2M12b22RhFZC81BZXSul-E2lleb5eOnGCBI3jBwALKWReJOpuZ85w9rvpqp3evN4MrDffjp70vbcG7K9ebXx6GHxAT5v0iftCkaMQ&3D%3D was there which successfully connects the Google account on account.The actual fishy behaviour:
The last redirection to
/account/social-connect/google/0b96f5c3ef391a5cQxHZRTXgbdN9ibq3NbFBxzsBYuwt3TeyFT87rVCdAQDyF6m32u9ABHs1WHOHfzYWKd5AWBOvcM5PzcdCoifAsVWrvyVES7vj6zgmPdlPEcf7o0VjFHWViUtUqGxzSALbziATACzBgJZcGanJf65NRhNiOqMfuZ1Y00iw_WV7WNOdxzwAw4bzI9q8hL3JaJI7BwZ67MDs8yHXmIn4ox014T9QAxkj4NRaVOZBDcXn-SDd1E4aSxcE5etFsmt1035VYw41MVFLK_KHidUDuXXd-x5EYc045V_XznxQsSUMuPfzkqvycQ3MkB6fOoiL6_mxqDt0eMlmWEJv7ILAfKm6ZllyBGBfLZ-XvZOnrm549x8yvw0hH2M12b22RhFZC81BZXSul-E2lleb5eOnGCBI3jBwALKWReJOpuZ85w9rvpqp3evN4MrDffjp70vbcG7K9ebXx6GHxAT5v0iftCkaMQ&3D%3D was actually fishy for me.If you have tested this kind of issues, then you might have noticed that while connecting to 3rd party applications, generally there only 2 requests occur i.e. a
GET request to google which consequently returns an auth code & another request to the target server with that same auth code returned by Google. Let's take an example of Chess.com, it also follows the same order:But in the case of target.com, there was a 3rd redirection which contains a secret code generated by , not by Google. I immediately unlinked that google account & sent a GET request to that 3rd redirection location i.e.
https:// .com/account/social-connect/google/0b96f5c3ef391a5cQxHZRTXgbdN9ibq3NbFBxzsBYuwt3TeyFT87rVCdAQDyF6m32u9ABHs1WHOHfzYWKd5AWBOvcM5PzcdCoifAsVWrvyVES7vj6zgmPdlPEcf7o0VjFHWViUtUqGxzSALbziATACzBgJZcGanJf65NRhNiOqMfuZ1Y00iw_WV7WNOdxzwAw4bzI9q8hL3JaJI7BwZ67MDs8yHXmIn4ox014T9QAxkj4NRaVOZBDcXn-SDd1E4aSxcE5etFsmt1035VYw41MVFLK_KHidUDuXXd-x5EYc045V_XznxQsSUMuPfzkqvycQ3MkB6fOoiL6_mxqDt0eMlmWEJv7ILAfKm6ZllyBGBfLZ-XvZOnrm549x8yvw0hH2M12b22RhFZC81BZXSul-E2lleb5eOnGCBI3jBwALKWReJOpuZ85w9rvpqp3evN4MrDffjp70vbcG7K9ebXx6GHxAT5v0iftCkaMQ&3D%3D from another account & boom, my Google account got directly linked to my another account.The attack scenario:
Now the attack scenario is quite simple:
- The attacker goes to their account and connects their Google account.
- The attacker grabs the third redirection URL and unlinks their Google account from their account.
- The attacker then sends the third redirection URL to the victim. Once the victim clicks on it, a
GETrequest tohttps:// .com/account/social-connect/google/0b96f5c3ef391a5cQxHZRTXgbdN9ibq3NbFBxzsBYuwt3TeyFT87rVCdAQDyF6m32u9ABHs1WHOHfzYWKd5AWBOvcM5PzcdCoifAsVWrvyVES7vj6zgmPdlPEcf7o0VjFHWViUtUqGxzSALbziATACzBgJZcGanJf65NRhNiOqMfuZ1Y00iw_WV7WNOdxzwAw4bzI9q8hL3JaJI7BwZ67MDs8yHXmIn4ox014T9QAxkj4NRaVOZBDcXn-SDd1E4aSxcE5etFsmt1035VYw41MVFLK_KHidUDuXXd-x5EYc045V_XznxQsSUMuPfzkqvycQ3MkB6fOoiL6_mxqDt0eMlmWEJv7ILAfKm6ZllyBGBfLZ-XvZOnrm549x8yvw0hH2M12b22RhFZC81BZXSul-E2lleb5eOnGCBI3jBwALKWReJOpuZ85w9rvpqp3evN4MrDffjp70vbcG7K9ebXx6GHxAT5v0iftCkaMQ&3D%3Dwill be sent with victim's session, and the attacker's Google account will be added to the victim's account. - The attacker then uses the "Login with Google" functionality to easily access the victim's account.
This results in a simple one-click account takeover vulnerability.
Please note that this information is provided purely for educational purposes. You are solely responsible for any misuse of any vulnerabilities.